Acumatica Multi-level Security
- Public or private hosting options
- Role based access to screens, fields, inquiries, and reports
- Data input and accessibility valid only through Acumatica business logic
- Complete audit history for logins, logouts, screens accessed, emails sent, and more
- Web Application security solution continuously monitors and protects against malicious attacks
- Single-Sign-On (SSO) and Multi-Factor Authentication (MFA) user account protection
- Advanced Encryption Standard (AES) and TLS 1.2 encryption algorithms for data transmission
Acumatica Security Highlights
Authorize user access via a unique login name.
Ensure consistent security and identity experiences to minimize friction for developers and business initiatives and reduce organizational risk from cyberattacks by implementing end-to-end identity management, data protection, strong authentication, trust validation, cloud security, compliance, two-way data monitoring, and data encryption.
Comply with the European Union’s General Data Protection Regulation by tracking a user’s consent to store and process private information and hide or completely erase it if consent expires.
Technologies supported include Active Directory (AD), Microsoft Active Directory Federal Services (AD FS), Microsoft Entra ID (formerly Microsoft Azure Active Directory), and providers that support Open ID Connect (such as Google, OneLogin, Okta).
Assign user accounts to UI, API, or Unrestricted types. UI accounts access the system via the application user interface login screen, API accounts via web services, and Unrestricted accounts via the UI, web services APIs, or OAuth 2.0
Assign access rights to specific application areas, including forms, containers of form elements, and form elements. Configure user access rights through roles, user logins, or application screens.
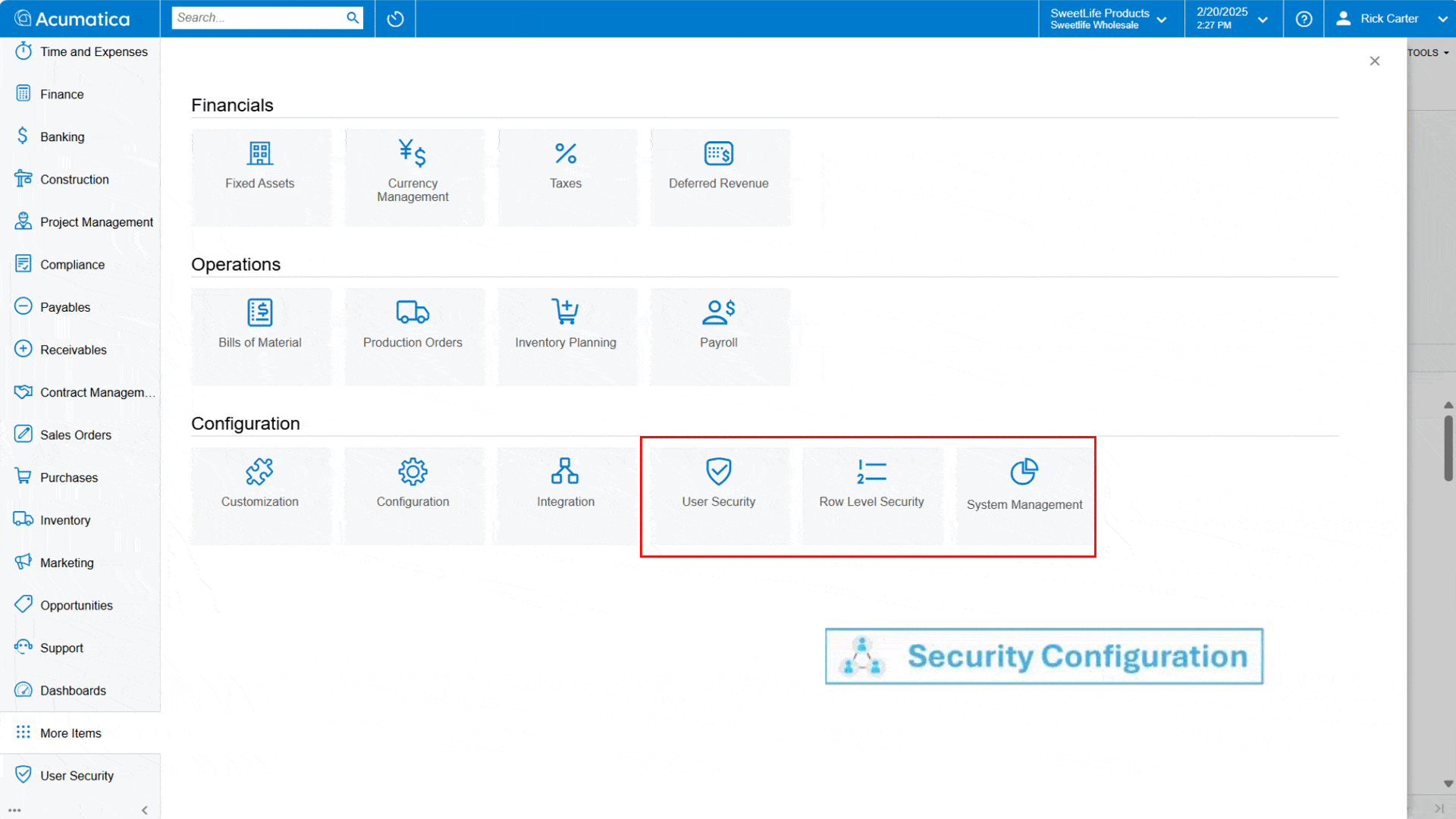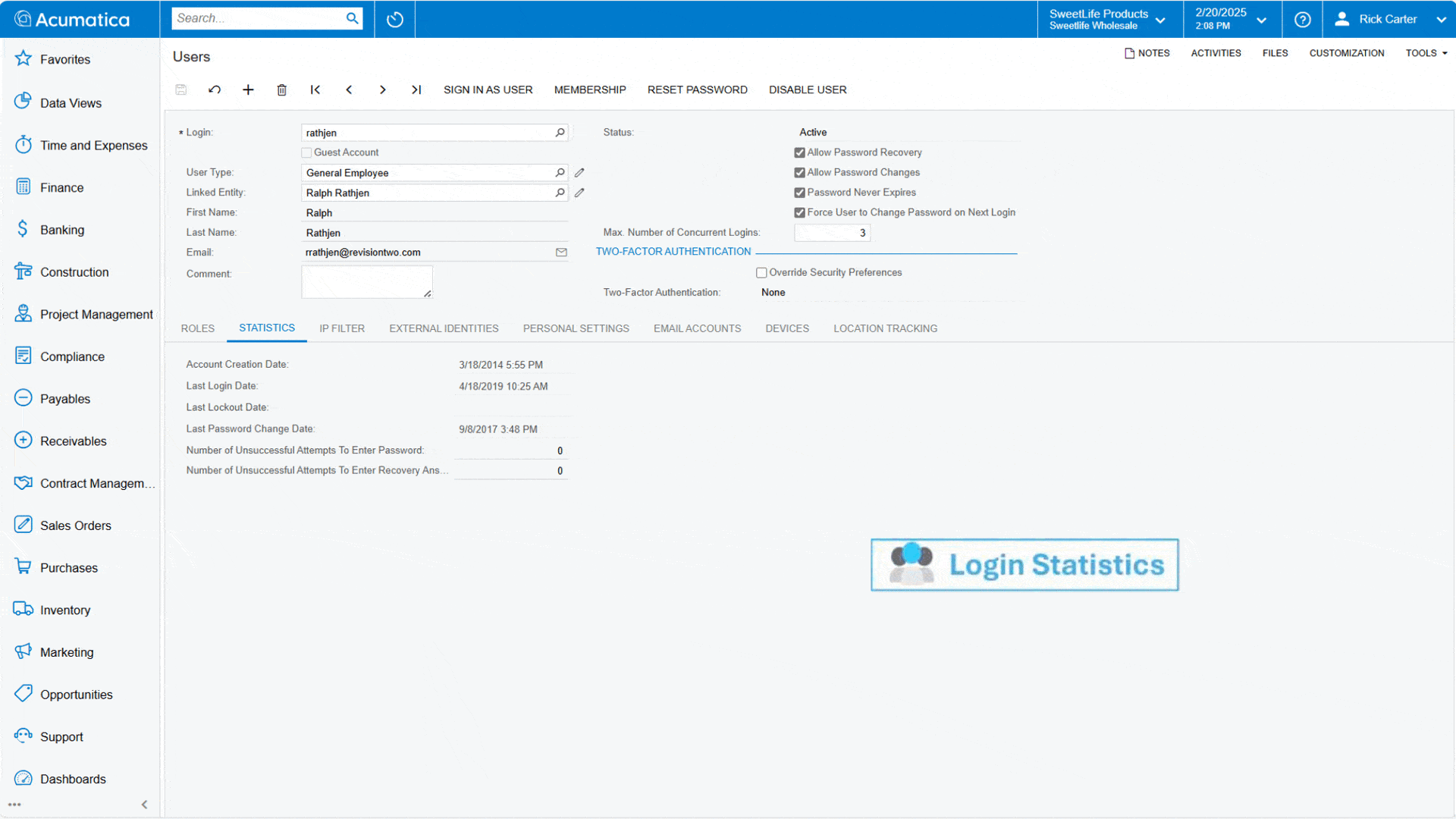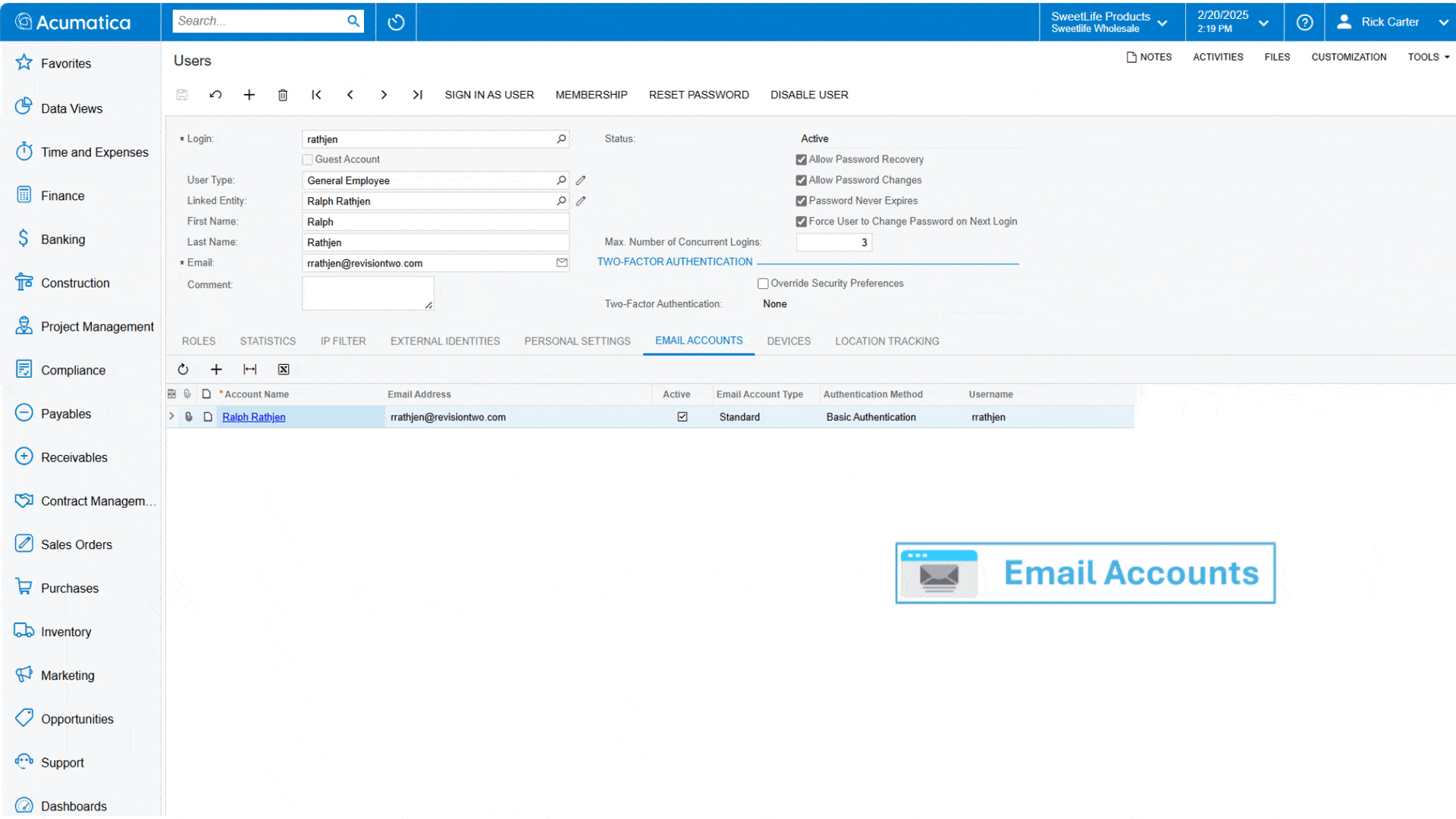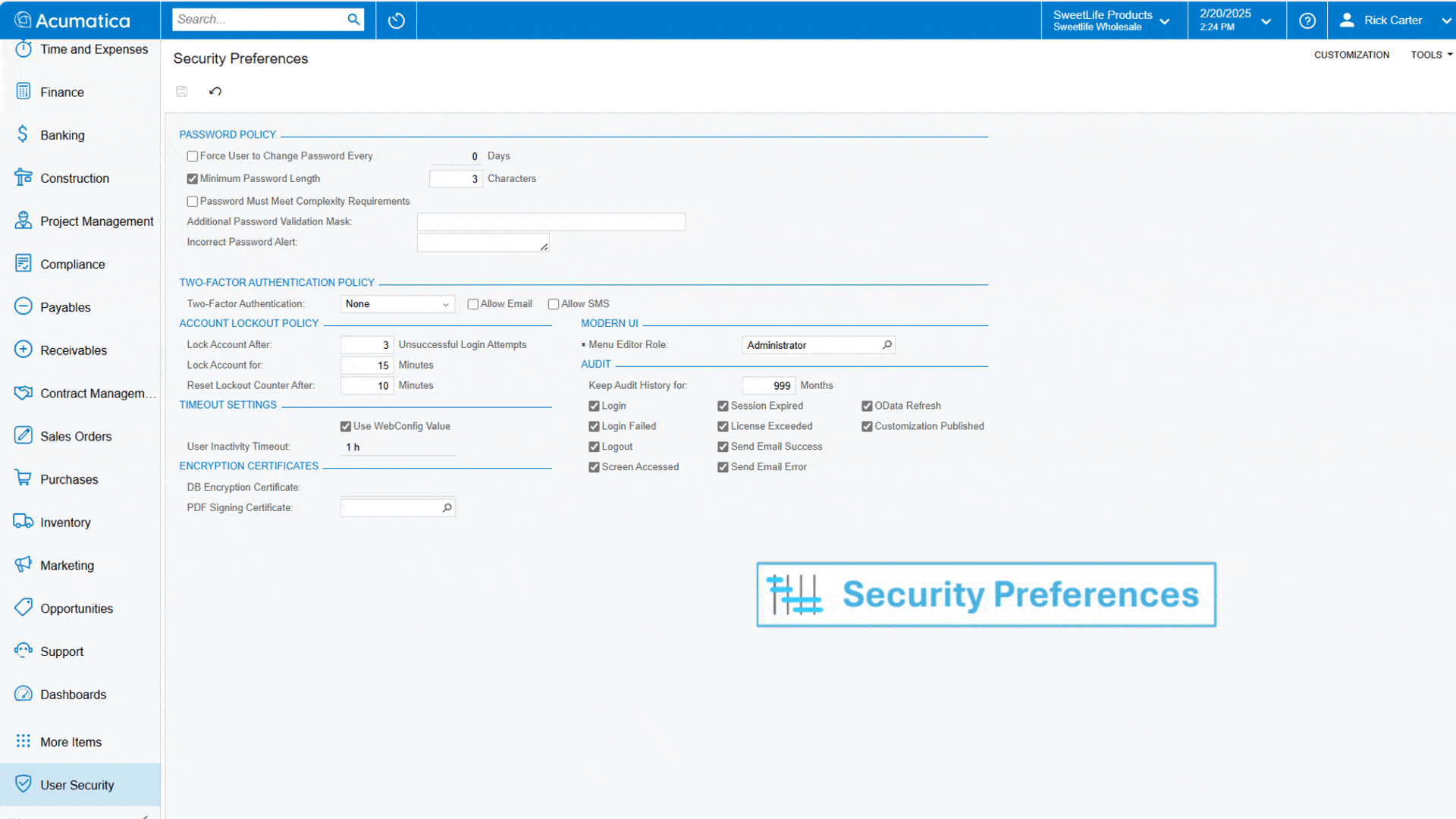
Configure two-factor authentication (2FA) to permit system access only after a user provides additional evidence of authentication through email or sms or enable 2FA push notifications with the Acumatica Mobile App.
Define security settings for your organization, such as system passwords and lockout policies for unsuccessful login attempts, encryption certificates, and audit settings.
Establish password policies for your user community including employees, customers and APIs, including specifying time intervals that require users to change their password, minimum password length and complexity, password validation mask, and a message for incorrect password entered.
Limit logins by listing the range of IP addresses that are granted access to the system. Login access is denied for IP addresses outside the range specified for the user account.
Gain visibility into mobile devices used to sign into Acumatica. Mobile devices that access the system are automatically registered with the user’s login account.
Protect PC and mobile device data when in a public IP location, such as a coffee shop, airport, etc.
Secure data in transit with either an Acumatica or Customer provided TLS certificate.
Specify the time interval of user inactivity before requiring re-sign-in, as set in the web config file. Default: 1 hour, Minimum: 15 minutes, Maximum: 8 hours.
Define the number of months to retain the audit history of user operations.
Link user login accounts to employees or exiting contact accounts in the system.